Although many websites and services will inform you when there has been a data breach, it doesn’t always happen. Check Have I Been Pwned to see if your email address has been part of a compromise.
Tag Archives: Cybersecurity Tips
December’s Cybersecurity Focus: Charity and Disaster scams
Are you following the Israel-Gaza crisis in the news and want to help by donating to a charity? Scammers follow the news, too, and are at the ready. Just like in the wake of a natural disaster, scammers set up fake charities and fake websites to take advantage of your generosity. Here’s how to avoid charity scams and make sure your donation counts.
First, slow down and take some time to research and plan before you donate to make sure your money helps real people in need and not the charity scammers.
Here’s where to start:
- Donate to charities you know and trust with a proven track record with responding to a humanitarian crisis.
- Research the organization — especially if the donation request comes on social media. Search the name plus “complaint,” “review,” “rating,” or “scam.” And check out the charity with the Better Business Bureau’s (BBB) Wise Giving Alliance, Charity Navigator, Charity Watch, or Candid. If the message was from a friend, ask them if they know the organization themselves. Find out exactly how much of every dollar you donate goes directly to the charity’s beneficiaries.
- Be cautious about giving to individuals on crowdfunding sites. Some scammers pretend to be concerned citizens collecting for a cause but their true intentions are to pocket your money rather than give it to the cause. Giving to someone you personally know and trust is safest. Review the platform’s policies and procedures. Some crowdfunding sites will check out postings asking for help after a humanitarian crisis to confirm they’re legit. Others don’t.
- Donate money rather than goods unless you confirm what’s needed. If you want to send goods like clothing or supplies, it’s a good idea to confirm with the charity what items they are collecting.
- Don’t donate to anyone who insists you pay by cash, gift card, wiring money, or cryptocurrency. That’s how scammers tell you to pay. If you decide to donate, pay by credit card, which gives you more protections.
- Confirm the number before you text to donate. Go straight to the charity to confirm the number. If it’s not their number, use a number you know is real or go to the charity’s website to donate.
To learn more, go to ftc.gov/charity. Source: https://consumer.ftc.gov/consumer-alerts/2023/10/safely-donating-response-israel-gaza-crisis
Phishing, Rogue Sharkpass/DUO pushes, and Job scams

Some of you may have received a Phishing Email with the subject “A file has been shared with you”, or something similar. This email “appears” to be coming from someone within Simmons or even from an external email address. Clicking the link brings the victim to a web page that looks like an official-looking webpage and asks them to enter their username and password. Once that information has been entered on the webpage it is captured by the cyber criminals.

Almost immediately following, the cybercriminals attempt to login to Simmons’s email and systems with the stolen credentials and the victim will receive a Duo authentication request known as a “Rogue Push”, meaning one that was not requested. If the victim approves the Duo request, then the cybercriminals are allowed in. Think before you click!
The Job Scam is intended to steal money from the victim in one of two ways. The first is that they ask for personal information plus a bank name. They will then send an official looking email from that bank asking the victim to confirm details and maybe to reset a PIN code. The scammers will try to use this information to login to the bank account and withdraw money. The second way is to send the victim a paycheck in advance with instructions to use that check to purchase supplies or a computer from their vendor. The victim purchases these items before the bank has time to clear the deposited check. The fake check will bounce and the victim is left responsible for the purchases. Other variations of this scam have involved sending cryptocurrency such as bitcoin to the scammers.
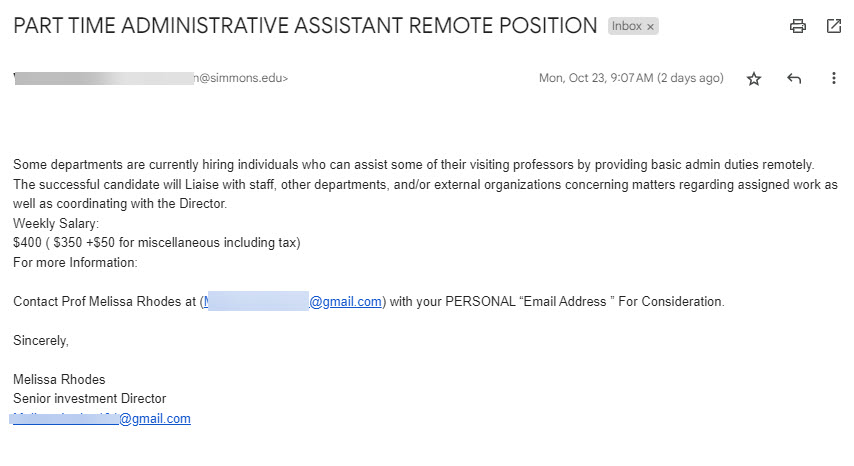
As phishing and job scams targeting higher education persist, vigilance is key. Carefully inspect unsolicited emails and do not click links or provide information without verifying legitimacy first. Report suspect message as phishing in Gmail. Research employers thoroughly when job hunting and avoid requests for upfront fees or personal details. Never provide banking information. Stay alert and contact the IT help desk with any online safety concerns. Using caution and common sense are our best defenses against those looking to take advantage.
Holiday Cybersecurity Tips
 As the holiday season is underway, Simmons Technology is reminding users to be cautious of potential holiday scams and malicious cyber campaigns, particularly when browsing or shopping online. These scams can come in the form of emails or ecards with malicious links, attachments infected with malware, or requests to support fraudulent charities or causes. It is important to remain vigilant and avoid clicking on unfamiliar links or providing personal information to untrustworthy sources.
As the holiday season is underway, Simmons Technology is reminding users to be cautious of potential holiday scams and malicious cyber campaigns, particularly when browsing or shopping online. These scams can come in the form of emails or ecards with malicious links, attachments infected with malware, or requests to support fraudulent charities or causes. It is important to remain vigilant and avoid clicking on unfamiliar links or providing personal information to untrustworthy sources.
It is important to take extra precautions to protect yourself against common online shopping scams. Here are some tips to stay safe:
- Only shop on reliable websites from retailers you know and trust.
- Avoid clicking on links in unsolicited emails and be wary of email attachments.
- Never give out your financial or personal information via email or text.
- Watch out for fake package tracking emails, fake ecards, and fake charity donation scams.
- Look for “https://” in the address bar before entering your credit card information online.
- Don’t auto-save your passwords or credit card numbers.
- Regularly check your credit card and bank statements and report any discrepancies to your financial institution.
- Use text alerts provided by your banking app or site to help detect unusual activity.
- Pay with a credit card instead of a debit card, as credit cards offer protections that may reduce your liability if your information is used improperly.
- Ignore pop-up offers and deals, and make sure your devices, apps, and anti-virus software are always up-to-date.
- Protect your passwords by making them long and strong, never sharing them with anyone, and using two-factor or 2-step authentication whenever possible.
We encourage users to remain vigilant and stay safe during the holiday season.